Featured
Table of Contents
Understanding Vpn Protocols: Openvpn, L2tp ...
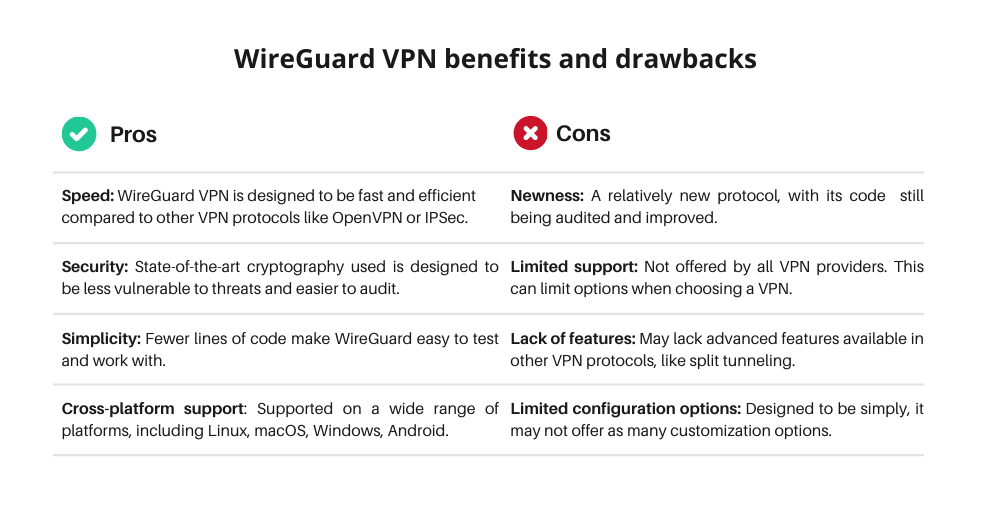
One of the most popular VPN services,, was the first of the larger VPNs to use Wire, Guard's protocol. Nord, VPN believed so extremely of Wire, Guard that it took things even more and modified the open-source offering to develop Nord, Lynx, its customized protocol that uses one of the fastest VPN connections.
When comparing Open, VPN and Wire, Guard, it is essential to consider the strength of encryption but likewise speed, and versatility in regards to how quickly it can be incorporated into various networks. is an open source protocol that was developed in 2001, and regardless of its age most encryption tools support it, therefore it has ended up being the most popular of all VPN alternatives on the market.

How do I setup Wire, Guard? Setting up a Wire, Guard application is simple.
What Is Nordlynx And How Does It Work? [Full Explanation]

What's much better: IPSec vs Wire, Guard? There are many reports that Wire, Guard provides the very same level of file encryption while making connections quicker, but some enterprises might choose IPSec due to the type of cryptography algorithms it supports.
There are numerous totally free VPNs that support Wire, Guard, and it is also consisted of by default in the Linux kernel, so those who are adept at programs can develop these kinds of encrypted connections merely by typing in the command line. Wire, Guard is likewise supported by subscription-based security products.

After that all connections will be tunneled utilizing Wire, Guard rather than alternative protocols. Is Wire, Guard safe to utilize? It is relatively brand-new on the scene, Wire, Guard's tiny codebase has been thoroughly evaluated and audited, and it's inclusion on the Linux kernel is a massive vote of self-confidence in its safety.
Wireguard Protocol Now Powered By Fastestvpn
Many VPN options that exist today were created a long time earlier, so they're rather sluggish and are excessively engineered. Enter Wire, Guard, a job that puts security and simplicity first. Security researcher and kernel designer Jason Donenfeld got the concept for Wire, Guard in 2017 while in requirement of a stealthy traffic tunneling option that might be used throughout penetration testing engagements.
So, he set out to develop a completely new VPN procedure and execution that would avoid some of the design choices that changed other tunneling technologies into monster tasks with big code bases and numerous knobs and switches. For one, the Wire, Guard protocol does away with cryptographic agility-- the principle of offering choices among different encryption, key exchange and hashing algorithms-- as this has actually resulted in insecure releases with other innovations.
The protocol is also sneaky, as it does not react to any packages from peers it doesn't recognize, so a network scan will not expose that Wire, Guard is operating on a machine. what is wireguard protocol and how does it work?. The connection between peers, which can act as both clients and servers at the same time, go silent when there's no exchange of information.
Should Businesses Consider Wireguard?
The main Wire, Guard execution is for Linux and is available in the form of a kernel module. The code is meant to be easily auditable, with Donenfeld saying it can be read in an afternoon. Compared to Open, VPN which has more than 100,000 lines of code and depends upon Open, SSL-- another substantial codebase-- the Wire, Guard kernel module has around 4,000 lines of code and the crypto code is constructed into it.
Aside from some community-supported Android firmware projects that incorporated the Wire, Guard kernel module, the non-Linux Wire, Guard implementations run in userspace and don't gain from the same performance as the kernel execution. That said, they still manage to match or surpass Open, VPN in the majority of cases. what is wireguard protocol and how does it work?. The Wire, Guard kernel module is readily available in the package repositories of all major Linux distributions and even some customized ones.
6, released on March 29, 2020, Wire, Guard is one of the innovations that are built in by default. This is also considered Wire, Guard's very first steady release, or version 1. 0.0."The last several weeks of 5. 6 advancement and stabilization have actually been exciting, with our codebase going through a quick security audit, and some real headway in terms of entering into circulations," Donenfeld said in the release statement.
What Is The Wireguard Vpn And How Does It Compare To ...
Donenfeld accepted the compromise and was mainly satisfied with the outcome."It's not called 'Zinc' any more, and some of the style choices I liked aren't there, but I believe the lion's share of what we wanted exists, and a couple of other pieces need to be possible to upstream one at a time," he stated in a message to the Wire, Guard job's mailing list at the time.
From then on, things moved fairly fast, with several reviews, bug fixes and modifications in the course of a few months before the steady release. Windows does not supply a native TUN virtual gadget and while some motorists exist to attain this from projects such as Open, VPN or Soft, Ether, they were composed a long time ago and have numerous problems.
Even prior to reaching a stable variation Wire, Guard was already being utilized in production. Some business VPN service companies provide Wire, Guard servers and there are continuous efforts to build mesh networking tools around it. It is not yet "business ready" and it's uncertain if it will ever be since its designers are unwilling to add new functions that are only beneficial to a subset of users or cover edge cases since that's how other projects became overly complicated.
What Is Wireguard? Simple Explanation Of A New(er) Vpn ...
Business need to release and set up new software on a big number of computers in an automatic manner, but the distribution of public secrets amongst peers and crucial management are not covered by the Wire, Guard job itself and will have to be carried out as a separate tool.
Wire, Guard, which makes it more available than some exclusive technologies. Its open source likewise makes it much more friendly when setting it up on devices that do not support Wire, Guard natively.
Wire, Guard needs to be an option without any shadows of doubt. Wire, Guard works by on the VPN servers so that the information packets would not be mixed among its users. In principle, this can significantly threaten the user's personal privacy as this is among the crucial vulnerabilities that a trespasser could target.
Latest Posts
The 5 Best Vpn Services For The Bay Area
Which Vpn Is Best For My Business?
Best Free Vpn For Business In 2023