Featured
Table of Contents
Why Tor Is Worse Than Vpn
Unlike Tor, which only encrypts demands while utilizing the browser, VPNs are able to encrypt all the traffic coming from your computer system. This makes them more safe., the more protected variations cost cash.
Some VPN companies log your history while using their service. Try to find a declaration on your VPN's website to ensure they aren't collecting, saving or sharing any long-term identifiers of you. While both Tor and VPNs work to safeguard your online anonymity, VPNs are the most secure option if utilized properly.
Meanwhile, VPNs are quickly, encrypt all your traffic, offer you access to any Internet website and put you in control of your meant area. When browsing for the best VPN, make sure you install it properly and know how the company safeguards your data. The Panda VPN does not keep logs and walks you through appropriate installation.
Tor Vs Vpn: What's The Difference And Which Is Better In ...
Tor or VPN? The reality is, it's not an apples to apples comparison, and because you actually appreciate your privacy and security, I'm going to provide you a standard understanding of how each of these tools work and the specific jobs they're built for. Make certain to register for the All Things Secured You, Tube channel!.?.!! There's one crucial question you require to ask when choosing whether to use Tor or VPN.
Which's why a nuanced response is essential when comparing Tor vs VPN.Now I'm going to provide an overview comparison between Tor and VPN, and after that use another lesser-known option that combines the strengths of both of these tools into one. Some of the links in this short article may be affiliate links, which means that at no additional cost to you, I may be compensated if you pick to utilize one of the services listed.
I wrap it up in another envelope addressed to a various pal and don't put my return address on it.: When I give this envelope to the mailman, he doesn't know where the letter will ultimately end up, he just knows to deliver it to my friend. When my buddy receives the envelope, he does not know where it came from considering that it has no return address, all he knows is that when he opens it up, there are guidelines to provide it to my parents.
Tor Vs Vpn : Which One Should You Use In 2023?
Tor does have weak points. Let's take a look at a few of them.: Utilizing Tor is sluggish, and that makes sense if you consider all that's happening with the data when it passes through the Tor network.
Because The Tor Task publishes the complete list of exit nodes, there are a lot of online services that either block access to their site for anybody that comes from one of these exit nodes, or they force repeated security difficulties such as CAPTCHA and others steps. This means that when using Tor, rather of having freer access to the web, you might discover yourself a bit more restricted.
This indicates that any other app or information transfer on your device that does not go through this web browser does not get the privacy advantages of the Tor network. A system-wide or device-wide Tor connection is possible, but it's not going to be simple to establish for the average person.
Difference Between Tor Browser And Tor Over Vpn
Over the years, various security specialists and scientists have actually declared ways to compromise the integrity of the Tor network. Mind you, unless your communications are high value, it's unlikely anybody would make the effort to do this. The more likely situation is that, practically as if I had signed the letter to my parents.
Oh, and I forgot one last thing. Tor is complimentary (which is definitely a reward). This dependence on volunteers is precisely why the network hasn't grown extremely quick over the previous years and it brings up legitimate concerns about who owns these nodes and why they're prepared to take in the expense of running them for free.
I indicate, there is an extra layer of encryption that takes place in between you and the VPN server you connect to, however once your web traffic leaves that VPN server, the encryption is also gone, so take that for what it's worth. This is why it troubles me that a lot of the VPN market and many of the influencers and content developers who earn money here, tend to promote privacy and security as the primary selling points of a VPN.As I have actually explained in another post about why you need to stop utilizing a VPN, the truth is that a virtual private network is best utilized to avert censorship, protect your IP address and or gain access to georestricted content like Disney+, BBC i, Player and more.
Vpn Vs Tor - What's The Difference ? (Pros And Cons)
And there's always a risk it might be broken. I'm comparing the two side by side here, but as I stated at the very start, this truly isn't an apples to apples comparison. We're comparing a decentralized personal privacy tool, Tor, with a central secure gain access to tool, or VPN.If your information provides a risk to you, Tor is most likely your finest choice.
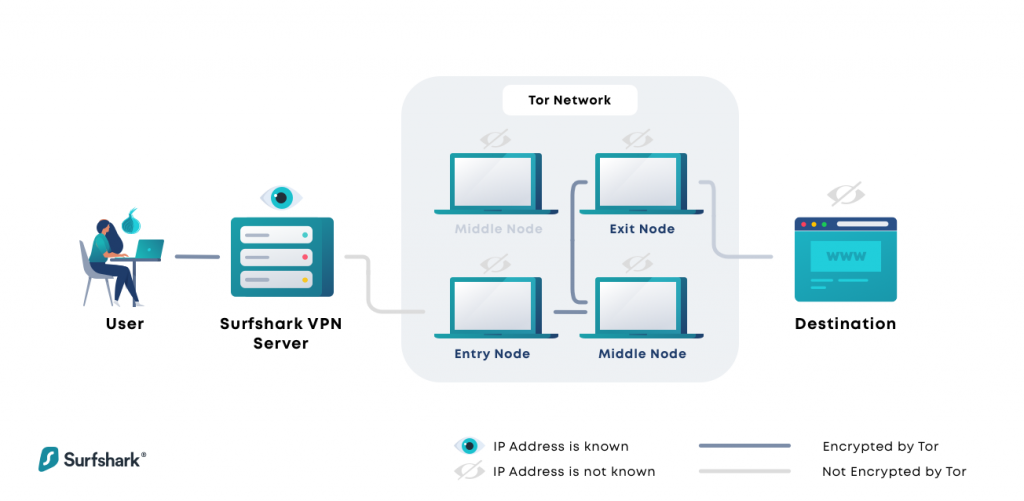
Let's take a fast appearance at some alternatives to Tor and VPN. There's what's understood as Tor over VPN, likewise called "Onion over VPN", where you're basically linking to a VPN first and then accessing the Tor network from there.
I use a service like Mysterium Network as my favored d, VPN and while it's still an innovation in its infancy, it has actually carried out well for me. I'm not here to declare a winner between Tor vs VPN or to tell you that you need to use one over the other.
Latest Posts
The 5 Best Vpn Services For The Bay Area
Which Vpn Is Best For My Business?
Best Free Vpn For Business In 2023